Using secrets in PyCafe
Often, when Python code is run at a server, it needs to access secrets, like API keys, or database passwords. Since the Python code of your PyCafe app is sent to the end user, it is not possible to keep these secrets private using techniques like environment variables. Make sure you do not include secrets in code is shared with others.
However, there are other ways to work with secrets.
Bring your own secrets
This can be especially useful for LLM based applications where you want the user of your program to provide for instance their own OPENAI_API_KEY, so you don’t pay for the API usage. Another use case is a demonstration application for your company’s API, where you want your clients to provide their own API key so they use their own data.
Asking the user for a secret
You can ask the user for a secret by using the pycafe.get_secret function. This function will prompt the user for a secret, and return it as a string. You can then use this secret in your code.
import streamlit as st
import pycafe
value = pycafe.get_secret("SUPER_SECRET_API_KEY")
st.write(value)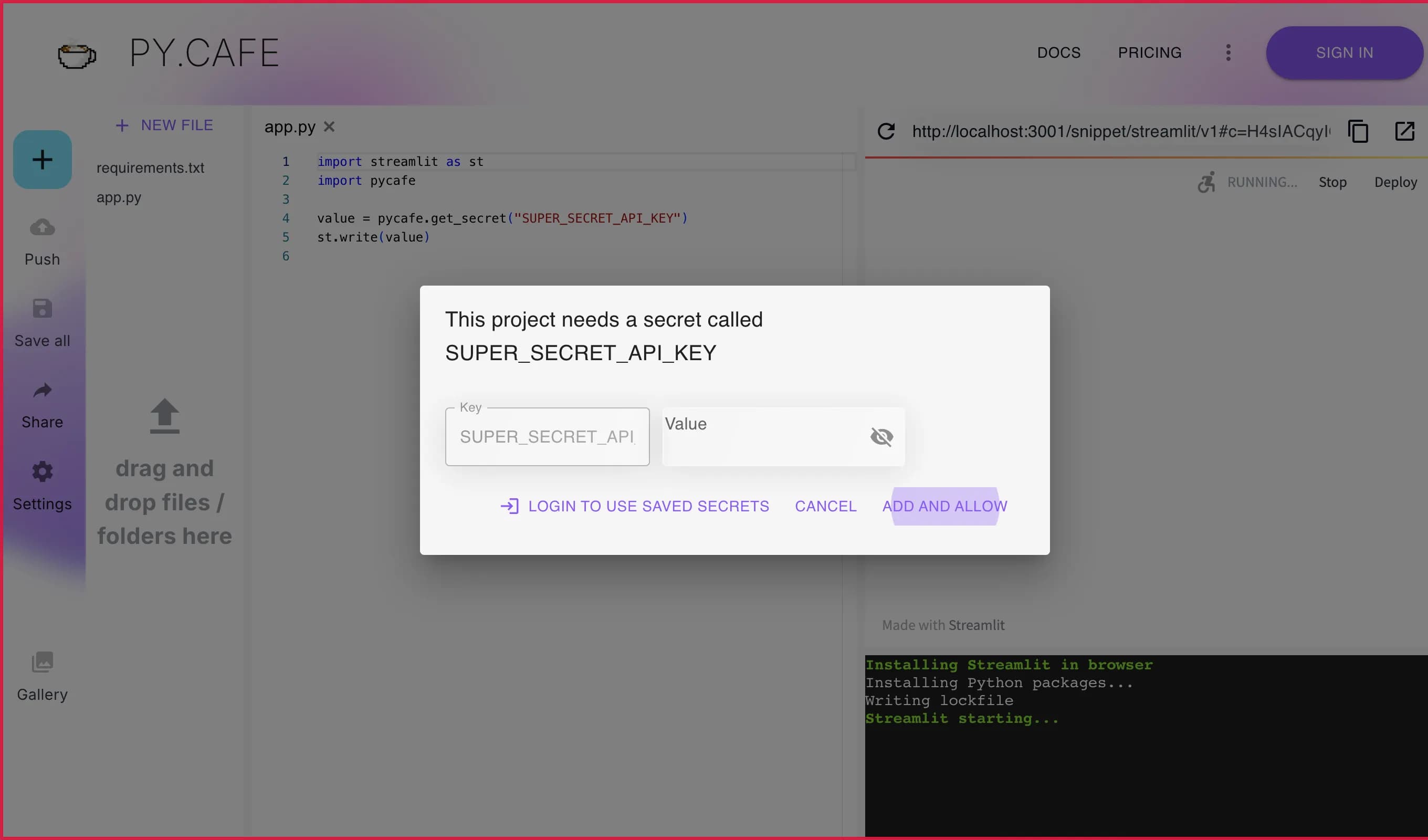
The first time, a user will see a prompt like this, where they can enter their secret:

After entering the secret, and clicking “Add and allow”, the secret will be stored in the browser (if not logged in), or securely in our database (if logged in), and the code will continue running with the secret. You can click the visibility button / to show the secret in plain text (not adviced if people can see your screen).

In this example, we print the secret to the screen, but you can use it in any way you like in your code.
Giving a reason for the secret
Instead of just requesting a user to enter a secret, you can also give a reason why you need the secret. You can do this by passing a second argument to the pycafe.get_secret function. This will show the user a dialog with the reason you provide.
Since the format is in Markdown, you can also give a link to a page where the user can get the secret from, such as a company dashboard page where they can get their API key.
import streamlit as st
import pycafe
reason = """We need an OpenAI API key to generate text.
Go to [OpenAI](https://platform.openai.com/account/api-keys) to get one.
Or read [this](https://www.rebelmouse.com/openai-account-set-up) article for
more information.
"""
api_key = pycafe.get_secret("OPENAI_API_KEY", reason=reason)
from openai import OpenAI
client = OpenAI(api_key=api_key)
completion = client.chat.completions.create(
model="gpt-4o-mini",
messages=[
{"role": "system", "content": "You are a concise and friendly assistant."},
{
"role": "user",
"content": "How cool would it be if we could run streamlit and dash in the browser?"
}
]
)
st.write(completion.choices[0].message.content)
st.write("Finished!")
Now, we also see why the program needs the secret, a link to where the user can get the secret from, and a link to more information about the secret.

Again, the secret will be store for future use, and the code will continue running with the secret.

Managing secrets
If you want to change a secret, or revoke the permission for an application to use a secret, you can do this in the secrets manager. Click on the Settings button on the left, then choose Manage Secrets.
Here you see and edit all your secrets, and give permission for the current project to use them.

How are secrets stored?
When not logged in
When you are not logged in, the secrets are stored in your browser, in sessionStorage. This means that the secrets are only available in the current tab, and are lost when you close the tab. This is a secure way to store secrets, as they are will not be stored for a long time, and are only available to you.
When logged in
When you are logged in, the secrets are stored in our database. This means that the secrets are available on all your devices, and are available when you log in on another device. We store the secrets in a secure way, since they are encrypted at rest (in our database), and the encryption keys are stored on a separate server as the data. We use a modern AES encryption algorithm with a 256 bit key, which is considered secure by modern standards.
Security details
If you want to know more about how we store secrets, here are some details:
- Encryption at Rest: Secrets are encrypted at rest in our database using a modern encryption standard, AES-256-GCM.
- Authenticated Encryption: We use AES-256-GCM, a mode that provides both confidentiality and integrity. This means your secrets are encrypted and also protected against tampering, thanks to an authentication tag that verifies data integrity.
- Separate Key Management: Encryption keys are stored on a separate server, which means that even if the database is compromised, the encryption keys are not available to an attacker.
By using AES-256-GCM, we adhere to industry standards for secure data handling.
What happens when I log in after I stored secrets?
When you log in after you stored secrets, the secrets are moved from your browser to our database. We merge the new secrets with the existing secrets, so you can continue using the secrets you stored when you were not logged in.